
To know what Blind SQL injection is. Let we first understand what normal SQL injection is. In normal SQL injection hackers depend on error messages returned from a database on a web page to find vulnerable databases.
The hacker can still execute SQL queries in URL and hack vulnerable database and get access to confidential information. This method we call it Blind SQL Injection. Though this method is slower and difficult, it is not impossible.
Let us assume that URL http://www.examplesite.com?id=5 is used to retrieve information about a user with id 5 from the database. The SQL query for this could look like this “SELECT * from user where id=’5 ‘“. The hacker can inject simple Boolean expressions into URL say. http://www.examplesite.com?id=5 OR 1=1 The SQL query for this could be “SELECT * from user where id=’5’ OR 1=1 “ If the server accepts and executes this query then it means that this website is vulnerable to SQL injection. Executing this query will return all rows from the table “user” since 1=1 is always true. By this way, a hacker can easily gain access to the user table.
Blind SQL injection has been recently discovering in one of the most popular SEO plugin – WordPress SEO Plugin by Yoast. More than one million websites use WordPress SEO Plugin. Wp Scan Vulnerability database (https://wpvulndb.com/vulnerabilities/7841) has responsibly disclosed the vulnerability to Plugin’s author. “The orderby and order GET parameters are not sufficiently sanitized before being used within a SQL query” In order to fix this issue all the websites using WordPress SEO Plugin <=1.7.3.3 are advised to upgrade to the latest version as this issue has been addressed and fixed. https://yoast.com/wordpress-seo-security-release/discusses the vulnerability and its fix.
The best way to prevent blind SQL injection is using prepared statements or parameterized SQL statements where the query is parsed only once and executed multiple times. 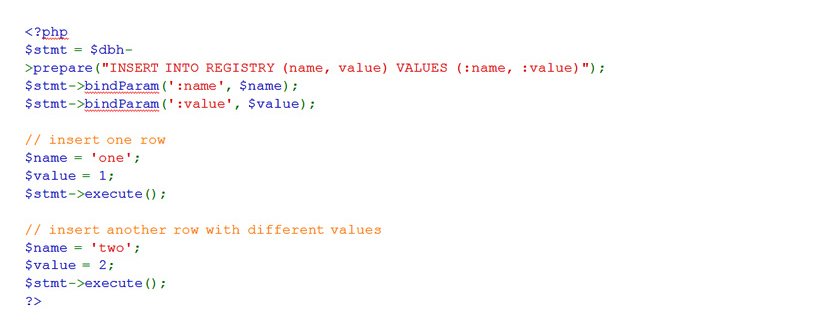 Learn more about PHP prepared statement http://php.net/manual/en/pdo.prepared-statements.php
Learn more about PHP prepared statement http://php.net/manual/en/pdo.prepared-statements.php
Below are the set of rules that will prevent most dangerous WordPress SQL injection attacks. 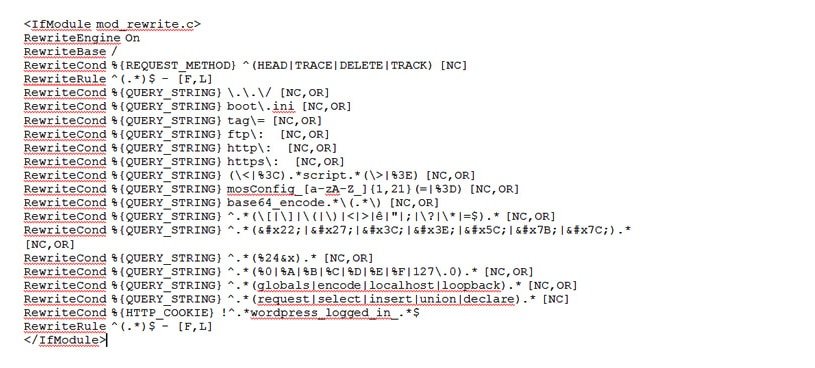
One of the most common ways to identify vulnerable websites is by using Google Dorks. Google’s “inurl” command is to find vulnerable words in the URL. You can find the list of google dorks here. http://1337mir.com/hacking/2013/10/google-dorks-sql-injection/ Here at Pattronize we strictly follow Data Sanitization methods http://codex.wordpress.org/Data_Validation#Database to develop highly secure WordPress themes and plugins. Your website is safe with us.
Stop putting everyone else first. Put yourself first. And go for it.
We're eager to work with you. Please share your project goals along with contact information. We will contact you within in 24 hours on business days. Really!